It has already been more than 2 weeks since Windows 10 (we’ll call it 10240, should save us some confusion) was publicly released, and a full month since Insiders first got the chance to see it. Still, there’s an interestingly small amount of information about what’s to come. Th1 is dead, long live th2.
We only have two post-10240 builds currently available – the officially released 10512 for Mobile and the leaked 10514 Windows Server build. Do they bring anything new (apart from the regular “seems faster” and “feels more stable”)?
Interesting exports
When comparing DLL Exports of 10240 and 10514, I noticed three new interesting exports. To be precise, they were CreateEnclave, InitializeEnclave and LoadEnclaveData from the kernel itself (kernel32.dll). These are definitely new, as neither 10240 for Desktops and for Mobiles had it, but both 10512 and 10514 already do. So what are these enclaves exactly?
A bit of disassembling
After installing the Windows SDK, doing live kernel debugging, kernel debugging over serial, kernel debugging over network, trying to dump memory, actually dumping memory, and then finding out there is a simple app that does dump the SSDT automagically (interestingly called NoVirusThanks SSDT View) and unlike my previous attempts actually works, I finally figured out where these exports (after a syscall) lead to. And what a surprise.
While the x64 Server binary had a lot of pretty complex assembly going on, the ARM version was way simpler.
ARM CreateEnclave
PUSH.W {R11,LR}
MOV R11, SP
LDR R0, =0xC00000F4 ;STATUS_INVALID_PARAMETER_6
POP.W {R11,PC}
ARM InitializeEnclave & LoadEnclaveData
PUSH.W {R11,LR}
MOV R11, SP
LDR R0, =0xC0000018 ;STATUS_CONFLICTING_ADDRESSES
POP.W {R11,PC}
As you can see (even if this is your first time when it comes to ARM assembly), the implementations are very dumb ones – they just return an arbitrary error code immediately, without doing anything serious. The x86_64 variants are however much more complex and actually implement stuff, so I won’t be going into further detail here.
Intel inside
So now we know that the enclaves are somewhat x86_64 specific, giving us a better idea what to google alphabet for. Soon, you’ll get to Intel® Software Guard Extensions (Intel® SGX). This set of new instructions enable the kernel to create an ‘enclave’. What is it good for?
If you don’t have a good understanding of what is kernel space and user space, I advice you to watch a great video on User Mode Isolation on Channel9 and then come back.
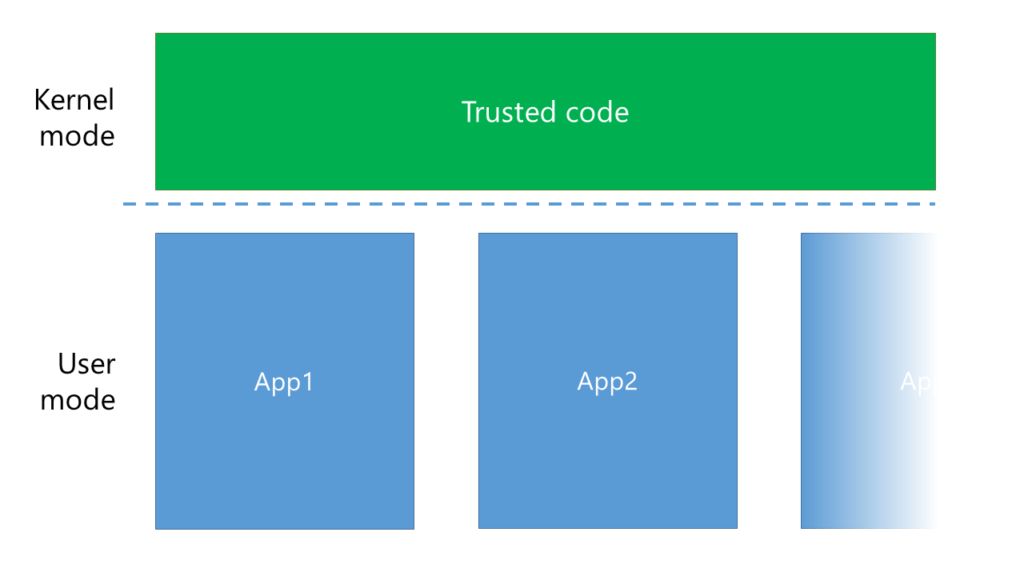
Until now, kernel mode was the “good guy”, while user mode was all these buggy, insecure apps. That’s why most of the focus was on isolating applications running in the user mode from one another, so your music player can’t touch memory of your browser with internet banking open.
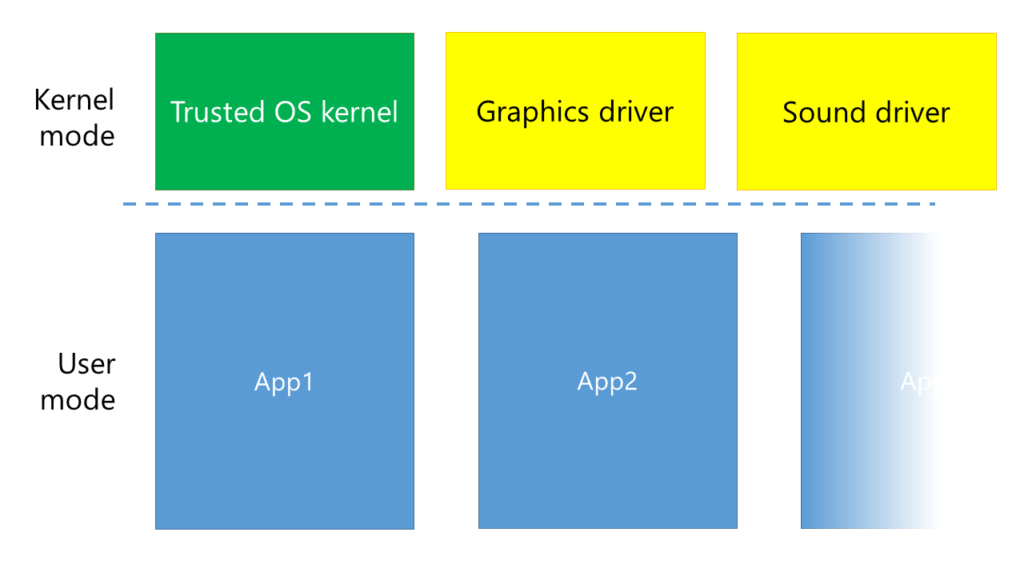
As you can see, every App has its own box and can’t access any other box. (It can, but it requires more effort and an approval of the kernel). However, what exactly is in this green “trusted code”? Turns out, it’s not just the operating system, it’s also drivers.
Problem is, these drivers are potentionally dangerous. Not only the unsigned ones (we all clicked “Install and continue”, didn’t we?), but also the tested and WHQL certified ones can have bugs and security holes. However, that dashed line between user mode and kernel mode provides no security whatsoever. If my sound driver wanted to touch the memory of any of my running applications, it could. And that’s where enclaves come to play.
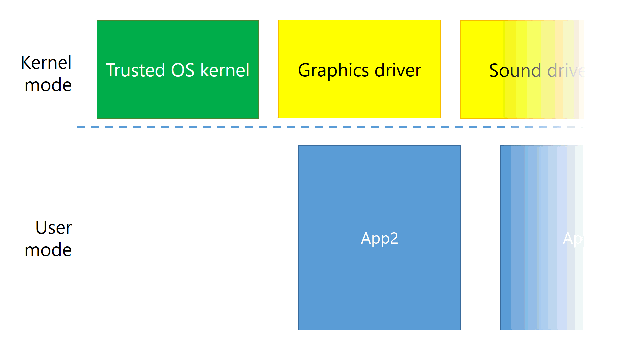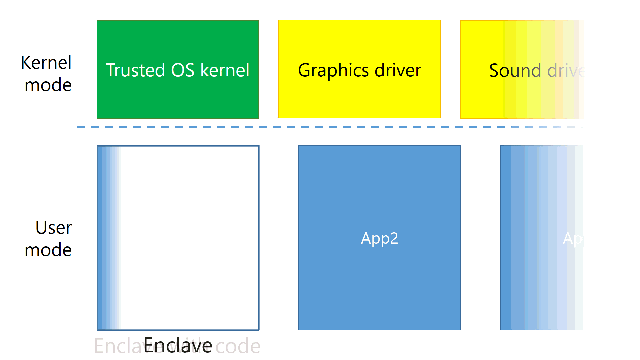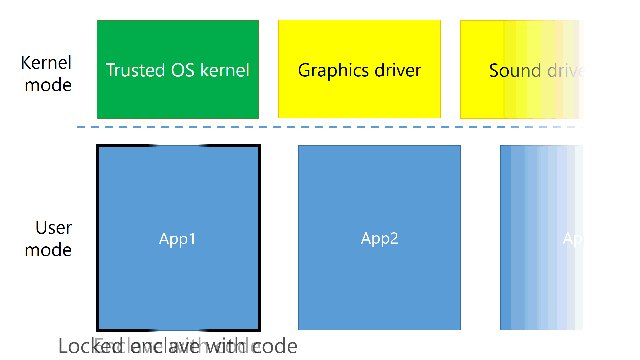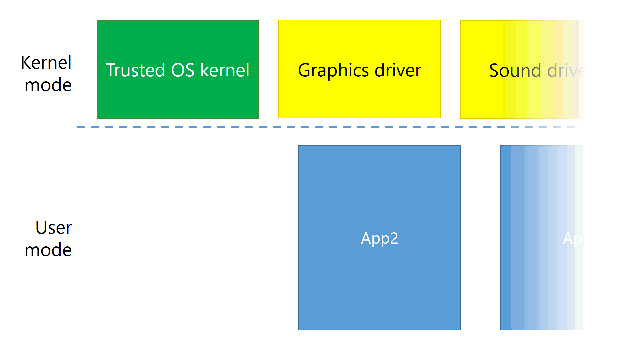
Think of enclaves as a small witness protection program. You lock the witness up, but mainly because you want to protect it from evil doings of somebody else. Here, the witness is your application and the evil is kernel mode code.
How does it work in practice? When you run an application, the kernel mode creates an enclave, fills it with the application code, locks it and tells the processor to run it. From the point it is locked, kernel mode can’t read or modify the application’s memory at all – it’s protected by hardware.
Conclusion
Yes, I know, it’s not much, but we are in the early days of Threshold2. I’ll make sure to update you once there’s a working example of working with enclaves, as at the current stage, no part of Windows is using it. Also, make sure to stay tuned, since we will make sure to take a deeper look at any future Windows 10 build that gets released!
Read more
Intel® SGX for Dummies (Part2) (Part3)
Secure execution of unmodified applications on an untrusted host (Microsoft Research)